Brief: In this review of Kali Linux, we try to answer some common questions: what is Kali Linux, what are the uses of Kali Linux and should beginners use Kali Linux or not?
Kali Linux has gained a lot of popularity recently. And there’s a reason for that. Hacking is back as the cool thing to do in popular culture and this can be attributed significantly to the TV series Mr. Robot.
Kali is one of the few hacking-focused Linux distributions, and Mr. Robot’s popularity has obviously helped Kali Linux attract new users. The graph below illustrates this.
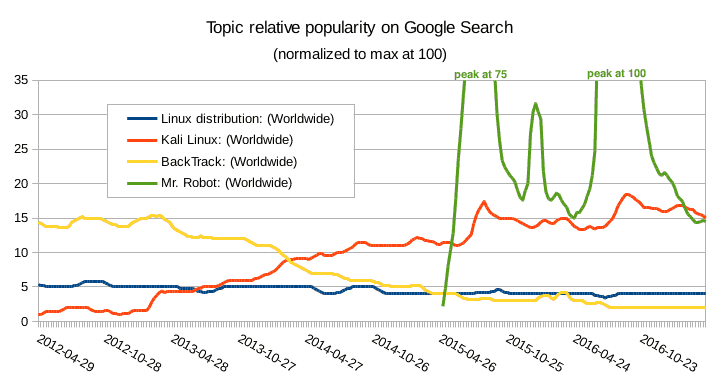
And with that, people with hardly any knowledge of Linux or anything related to computer security are now trying to use Kali as their main Linux distribution.
But Kali Linux was certainly not designed for general purposes. Look at the Kali Linux tools and you’ll find that many of them relate to “hacking”.
Of course, I could easily write an article explaining why it’s wrong to use Kali as a first Linux distribution. In fact, you could find great arguments here and here to dissuade you from using Kali unless you really have specific needs.
But I wanted to do something different. So I installed Kali Linux in VirtualBox and tried to put myself in the shoes of a “new user” trying some basic tasks on his brand new Linux system. Would I encounter some issues or would it be straightforward? Stay with me until the end of this article to read my conclusions.
What is Kali Linux?

Kali Linux is developed by the security firm Offensive Security. It’s a Debian-based rewrite of their previous Knoppix-based digital forensics and penetration testing distribution BackTrack.
To quote the official web page title, Kali Linux is a “Penetration Testing and Ethical Hacking Linux Distribution”. Simply put, it’s a Linux distribution packed with security-related tools and targeted toward network and computer security experts.
A Linux distribution is nothing more than a bundle containing the Linux kernel, a set of core utilities and applications and some default settings. So Kali Linux does not offer something unique in the sense that most of the tools it provides could be installed on any Linux distribution.
The difference is that Kali is pre-packaged with those tools and the default settings were chosen according to the intended use cases of that distribution, rather than, say, to fit the needs of the typical desktop user.
In other words, whatever’s your goal, you don’t have to use Kali. It is just a special distribution that makes the tasks it’s specifically designed for easier, while consequently making some other tasks more difficult.
Downloading Kali Linux— and checking the image integrity
To download Kali Linux, I went to the official download page and followed the first download link on that page.

Luckily, my computer is equipped with a 64-bit Intel CPU, so the amd64 image was the right one for my architecture.
In addition, on the download page, there were a bunch of hexadecimal numbers. Doesn’t that already feel “hackish”?
No, seriously, those aren’t there for fun. Kali Linux is intended to be used for security-related tasks. The last thing you want is that the tools you use are compromised somehow.
So, after downloading the Kali image, you should check the SHA-256 fingerprint of the file and compare it with the one provided on the download page. You can read this tutorial on how to verify checksums in Linux.
Now I can be confident in installing Kali Linux on my VM from that ISO image.
Kali Linux installation and initial experience
Kali Linux being based on Debian, the installation process is quite straightforward. And this is well documented on the Kali website.
For this test, I stuck as much as possible with the default options.
And only a few minutes later, I was able to boot into Kali Linux for the first time, ending up on this screen:
A user accustomed to Unix-like systems might be surprised to learn that “root” is the only user available after a default installation. But that’s because many pen-testing tools require super-user permissions.
Once again, this is a Kali-specific choice given its intended use case. But this is not the best choice for your everyday computer use (browsing the internet, using office applications, and so on). And it’s possibly the worst choice if you have to share your computer with someone else (more on that later).
Speaking of applications, the only ones installed on a default Kali Linux system are clearly oriented toward security. In addition to that, there are a bunch of command line tools not visible from the menu, and a few core utilities like a calculator, an image viewer and a couple of text editors. But you won’t find heavyweight office applications or productivity tools.
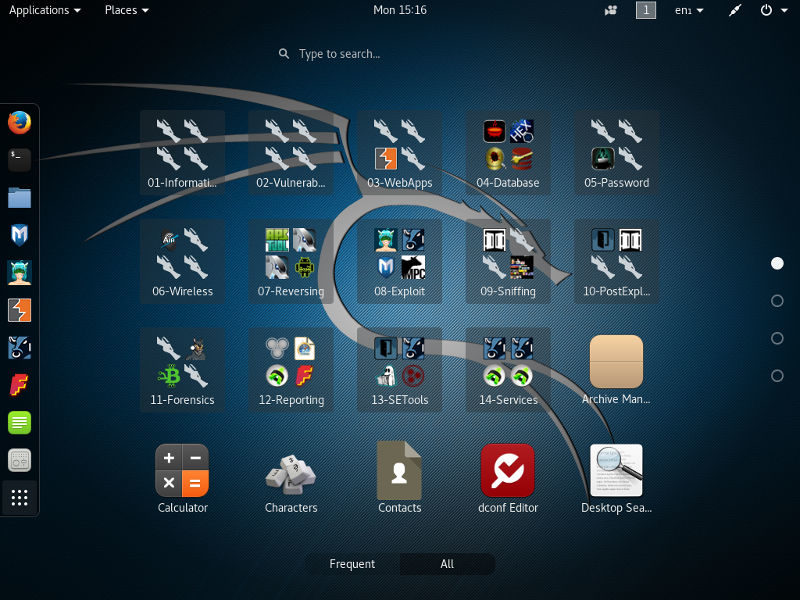
To give a concrete example, there’s no email reader as part of the standard installation. Of course, Kali Linux is based on Debian, and a lot of packages were ported. So you can install a lot of extra software by yourself and it should work:
apt-get update && apt-get install thunderbird
And indeed it will. But once again, is it really wise to check your mail as root on a machine you will use for security auditing?
[irp posts=”55197″]
What so “wrong” about working as root?
On a typical Unix-like system, users work as unprivileged users, with access to their own files, but without the ability to tamper with the system or other users’ files. For computer maintenance or to perform administrative tasks, some users may temporarily endorse the privileged identity “root” that gives them super-powers on the host.
On the other hand, on a default Kali Linux system, the only installed user is root and you have to work under that identity all the time. You have to understand that being root means there are basically no permissions checks on your machine. You can do anything you want. And even things you don’t want.
For example, when exploring your system you might inadvertently edit some critical files like /etc/passwd or some file in the directory /etc/grub.d/ in such a way that your system will become unusable. In some cases, you may alter your system without noticing any obvious changes until the next reboot or the next update – when it will suddenly break. And there are potentially hundreds of such critical files on a typical Linux system. The file permissions are set in such a way that an “ordinary” user couldn’t endanger the system as a whole. But being root for your daily work on Kali will remove that safety net (as it would on any Linux system, by the way).
Of course, nothing prevents you from creating new unprivileged accounts on your system. But this is extra work you have to do on Kali that you wouldn’t on another distribution – simply because you’re trying to use Kali for something it was not designed for.
Know what you do!
Somewhat in the same spirit, Kali Linux is packed with penetration testing tools: some of them are GUI tools, others are CLI tools. In both cases, it might be tempting to “toy” with them more or less at random.
But some commands may potentially be harmful to your home network. In addition, by not understanding the implications of what you are doing, you may put yourself in a difficult situation by using those tools at work or school, or on public networks. And in that case, ignorance will not be an excuse.
Again, this is not a Kali-specific issue: if you install penetration testing tools on Fedora or Linux Mint, and try random things with them, you may end up in the same trouble. Kali just makes that easier.
Kali is quiet – and it should stay like that
The first thing you can see on the Kali login screen is that motto: “The quieter you become, the more you are able to hear”. What does that mean?
If I listen on the network interface of my Debian system, I can see that it’s relatively noisy, sending network packets at more or less regular intervals. Some of them are sent by user applications, others by background services. And if I run nmap to perform a port scan on my regular desktop, I can see several open ports. Including a never-used vnc port and a long-forgotten HTTP server!
All of that because I have various services and user software installed. Some of them are part of my Debian default settings. Some are here because one day I installed a package and just didn’t remove it when I no longer needed it. This is the case, for example, for the HTTP server that I haven’t needed for weeks now but which is still currently running on my laptop.
On the other hand, Kali is designed to be as quiet as possible. This is required both to hide its presence on the network, and to harden itself against potential attacks. To achieve that goal, the default settings of Kali Linux disable many services that would be enabled on a genuine Debian system.
But, again, because Kali Linux is based on Debian, provided you enable the required packages, you should be able to install the services you want. For example, if you want to practice web development, you might be tempted to install a web server on your Kali host:
apt-get install apache2
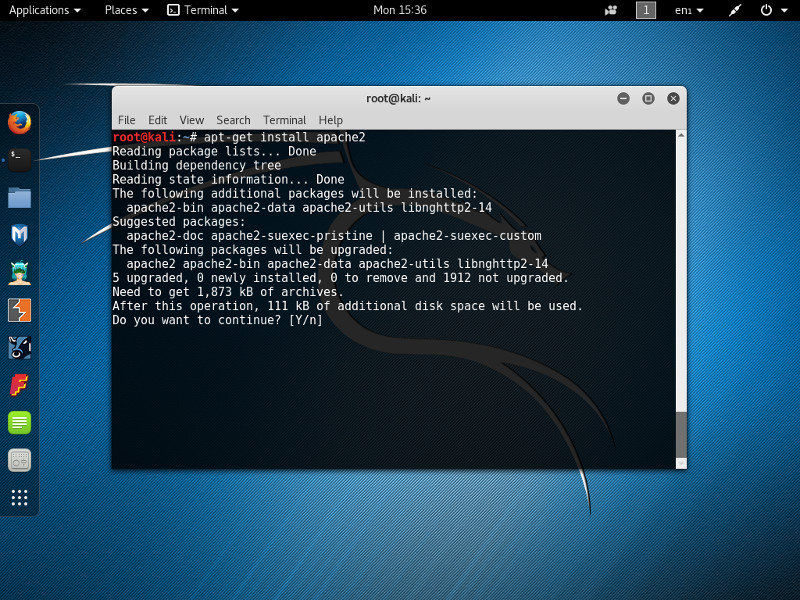
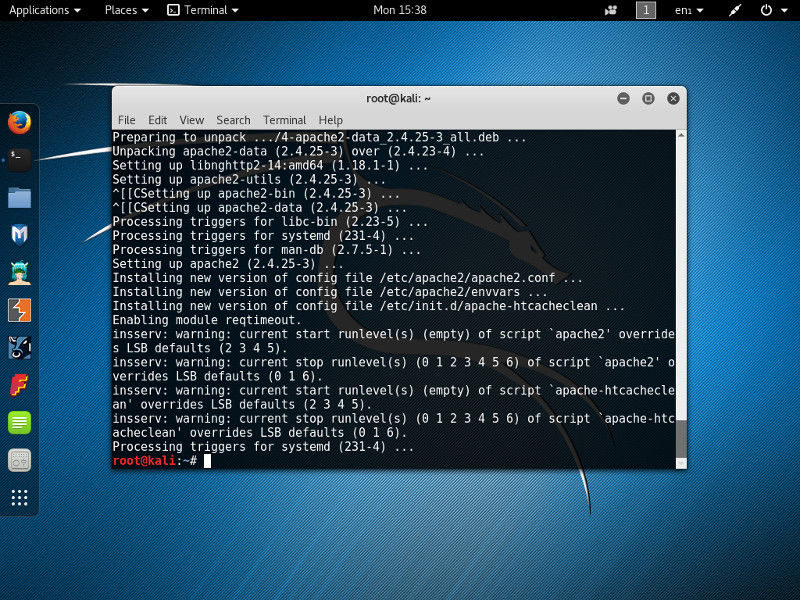
If you look closely at the command output, although it’s successful you may notice messages from insserv having some concerns about the “runlevels of script apache2”.
And indeed,
curl localhost curl: (7) Failed to connect to localhost port 80: Connection refused
Once installed, the web server is not started. You have to do it manually.
systemctl start apache2
And you will have to do it after each reboot: “Kali Linux, as a standard policy, will disallow network services from persisting across reboots by default.” (http://docs.kali.org/policy/kali-linux-network-service-policies)
Another option would be to change the policy in the /usr/sbin/update-rc.d file to whitelist apache2 as a startup service. But in that case, just like with my laptop, there are chances that you’ll leave that door open, even when you no longer need it. What could be a concern on my desktop system would be much more serious the day you plug your Kali system into a compromised network.
Don’t forget, one thing that makes Kali “special” is that it was specifically designed to work even when used in a very hostile environment. In that context, running a web server at startup on your Kali host defeats that purpose. In short, you’ve broken Kali. Maybe not visibly. But in spirit at least.
I need the software $prog but it’s not in the Kali repository!
There is no guarantee that all Debian packages are available on Kali. And there’s no guarantee that all possible software is available on Debian anyway.
So it could be tempting to add extra source repositories to your system to download more software than what’s provided by the official distribution. Or to add a repository providing the latest cutting-edge version of your favorite software. Here and there, you may even see “advice” suggesting that you modify the /etc/apt/sources.list file for that purpose.
Let’s be clear. If you consider doing that, a PPA-compatible distribution like Ubuntu will probably better suit your needs.
Not that I say you can’t add more source repositories to Kali Linux. But you shouldn’t: Debian warns us against what they call FrankenDebian as it can threaten the stability of your system.
And for Kali Linux it’s even worse. Not only could it break your system, but adding packages from an untrusted source to a security system is just nonsense. Even if you trust the source, keep in mind that Kali packages are hardened (you remember when I installed apache2 above?), which is not the case for most of the packages out in the wild.
Conclusion: Should you use Kali Linux?
And now it’s time for my conclusion. But I didn’t want to end that long article with a simplistic, black-and-white opinion. Especially as I don’t know you.
So here are three possible outcomes. Just pick the one that suits your case best:
1. If you jumped straight to this conclusion without reading the rest of the article, either you already have a strong opinion and I don’t have any chance of making you change it, or Kali is not yet for you. In that case, you should first consider a more mainstream distribution like a plain Debian system or Ubuntu. There will still be opportunities later to install the tools you need on a case-by-case basis.
2. If you read the article but skipped the parts containing too much technical jargon, Kali is not for you. Kali Linux could be an amazing teaching tool. But if you go that way, you have to be prepared for a steep learning curve. If you’re a very new Linux user starting from zero or if you just want to use your computer without headaches, there are plenty of general-purpose and user-friendly distributions to start with. Why not try Linux Mint or Zorin OS? Or maybe another Ubuntu derivative?
3. If you read the article, tried the commands I used, followed the links and looked the terms you didn’t understand – well, congratulations. You’re not just another “script kiddie”. On the contrary, you’re apparently ready to spend countless hours and effort to make your system work, understand the fundamentals of computer science and discover networking internals. That makes you one of the few new Linux users that could benefit from using Kali. But instead of using it directly on your computer, I would suggest that you first install some other Debian-based distribution and run Kali Linux in a virtual machine. That way you could practice your skills without sacrificing your other activities.
As the last word, maybe you disagree with me or didn’t recognize yourself in the three categories above – so don’t hesitate to use the comment section to give your opinion!

