
Nuking my system by installing Arch Linux was not enough, so I used a Fork Bomb.
Just kidding!
You might have already seen a cute looking but dangerous Linux command which is made of just special characters:
:(){ :|:& };:This is called bash fork bomb and it is enough to bring down your system by consuming all the system resources. It goes away after a system reboot, though.
In this article, I’ll discuss:
- What is a fork bomb in general
- How does the
:(){ :|:& };:turn into a fork bomb - Why the fork bomb is likely not to do any damage (yes, your distro might be bombproof)
- Quick tip on preventing fork bombs
What is a fork bomb?
You can think of a fork bomb as a DoS (denial of service) attack, as it replicates existing processes till your system utilizes 100% of system resources and makes it completely unusable.
Unix programs are executed through a combination of two system calls called fork and exec. One process spawns another either by replacing itself when it’s done — an exec — or, if it needs to stay around, by making a copy of itself — a fork.
The fork bomb is basically the process of creating forks after forks infinitely until your system doesn’t have anymore resources left.
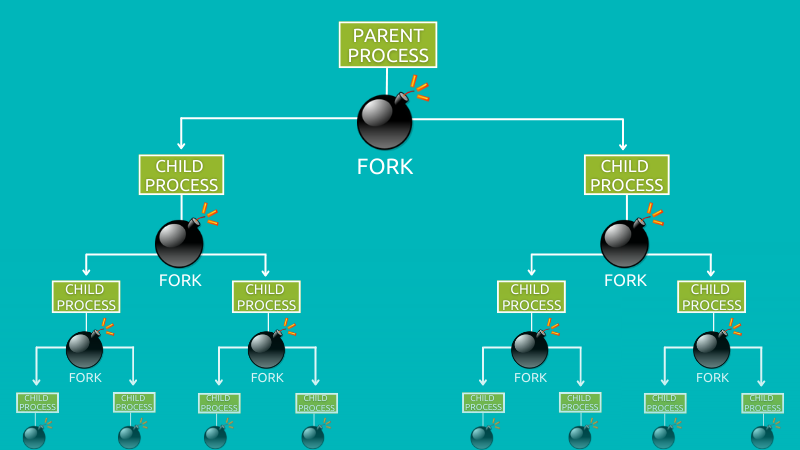
Of course, you can recover your system by rebooting, but the process is quite interesting!
:(){ :|:& };: is an example of such a fork bomb. It is popular because it’s made of just a few special characters, not long, complicated scripts.
Now, let me explain how this famous fork bomb works in Linux.
:(){ :|:& };: – How does it work?
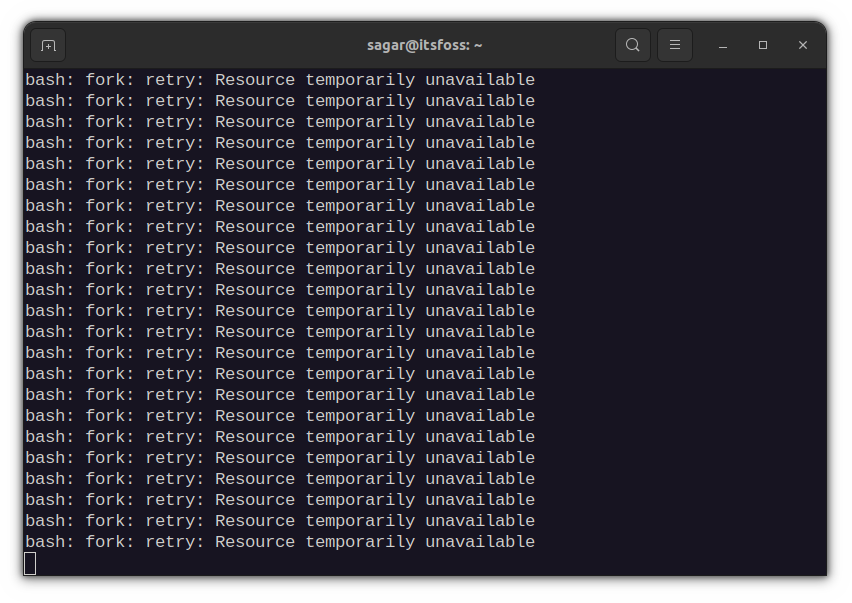
Well, this is what the famous fork bomb does to your system. And if you’re curious to know those 11 spooky characters, here you go:
:(){ :|:& };:As of now, you might have no idea how it works. Well, Let me break it down for you:
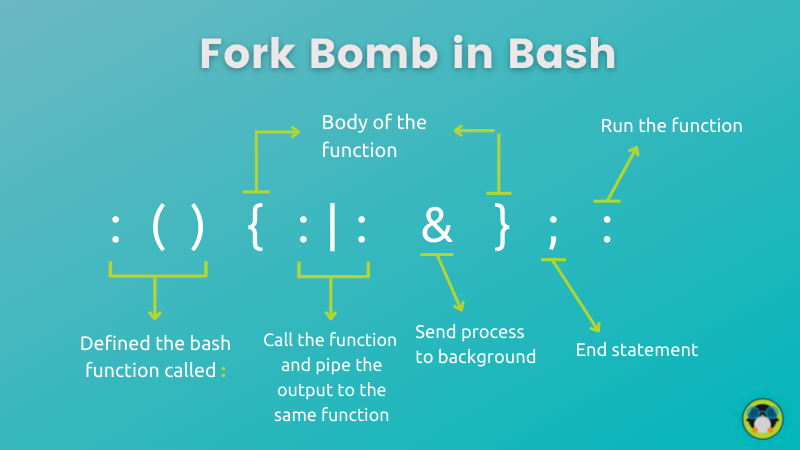
- :() defines the function named as
:and will accept no arguments. {}is where the function starts and ends. In simple terms, it includes commands that will crash your machine eventually.:|:is where the recursion starts (function calling itself). To be more precise, It loads a:function in memory, pipe (|) its own output to another copy of the:function which is also loaded into system memory as well.&will execute the whole function in the background so that no child process is killed.;separates each child function from the chain of multiple executions.- And
:runs recently created function, hence the chain reaction begins!
After going through the basics, I’m sure you want to surprise your friend with this attack. But I’d advise you to keep this attack to your virtual machine.
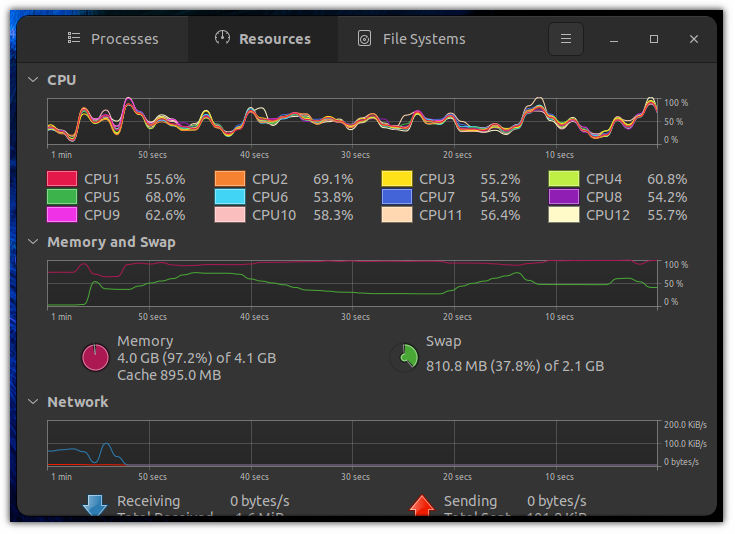
Oh! here’s a screenshot of the task manager when I ran the fork bomb in my testing.
Why does fork bomb not work in Ubuntu and some other distros?
Well, this is not limited to Ubuntu, but each distro that ships with systemd.
Systemd creates cgroup for each user which also defines the maximum processes. By default, it only allows users to have 33% of the whole.
Tinkering with systemd config is not suitable for everyday desktop users so if you’re interested I’d highly recommend you to check this answer on tweaking systemd config.
How to Prevent fork bomb?
As everything is related to processes, you just have to limit them. And the maximum processes that can run through a signed-in user can be checked through a given command:
ulimit -u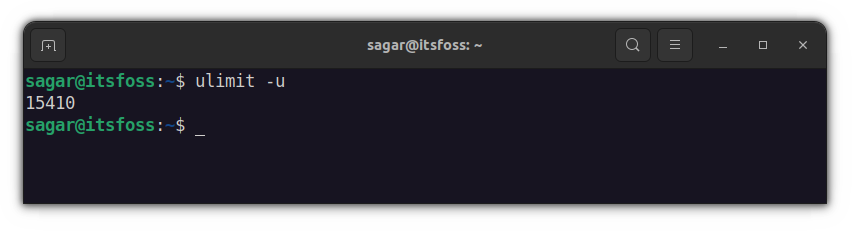
Mine is around 15k and any Linux user would have at least around 10k, which is much more than enough. So what you have to do is limit those background processes to around 5k, which should be plenty for most users.
ulimit -S -u 5000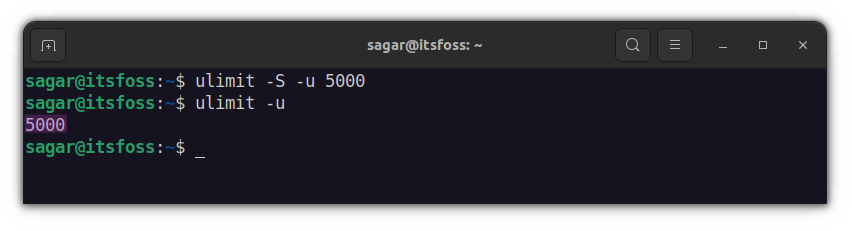
But this would only be effective for specific users. You can also apply this to the group by editing the /etc/security/limits.conf file. This is known to be a more effective way too!
sudo nano /etc/security/limits.confFor example, I want to apply this to all users who are in wheel group, so I’d be adding the following lines at the end of the config file:
@wheel hard nproc 5000Whereas for any specific user (sagar in my case) it would be this:
sagar hard nproc 5000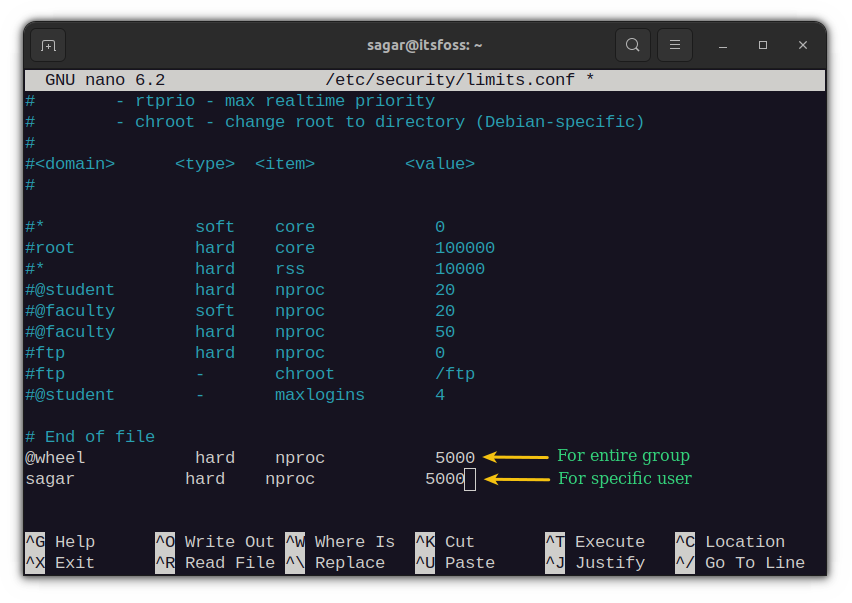
Conclusion
This fork bomb was created by open source software developer Jaromil. He thinks it is a work of art.
I kind of agree with Jaromil. It is indeed a work of art. Just 11 special characters and you get yourself a nasty program that has the capability to bring down a system.
I guess you have a better understanding of the fork bomb now. Let me know if you have questions or suggestions.
It's FOSS turns 13! 13 years of helping people use Linux ❤️
And we need your help to go on for 13 more years. Support us with a Plus membership and enjoy an ad-free reading experience and get a Linux eBook for free.
To celebrate 13 years of It's FOSS, we have a lifetime membership option with reduced pricing of just $76. This is valid until 25th June only.
If you ever wanted to appreciate our work with Plus membership but didn't like the recurring subscription, this is your chance 😃


