
It was not too long ago we talked about the first Rust CVE in the Linux kernel, which caused system crashes. That same day, 159 other CVEs were issued for C code. While that shows progress with Rust, it also highlights something more concerning; the kernel has bugs that hide for years before anyone finds them.
A research blog published on Pebblebed demonstrates how bugs often stay hidden for years before they are discovered and fixed.
The Linux Kernel Isn't Perfect
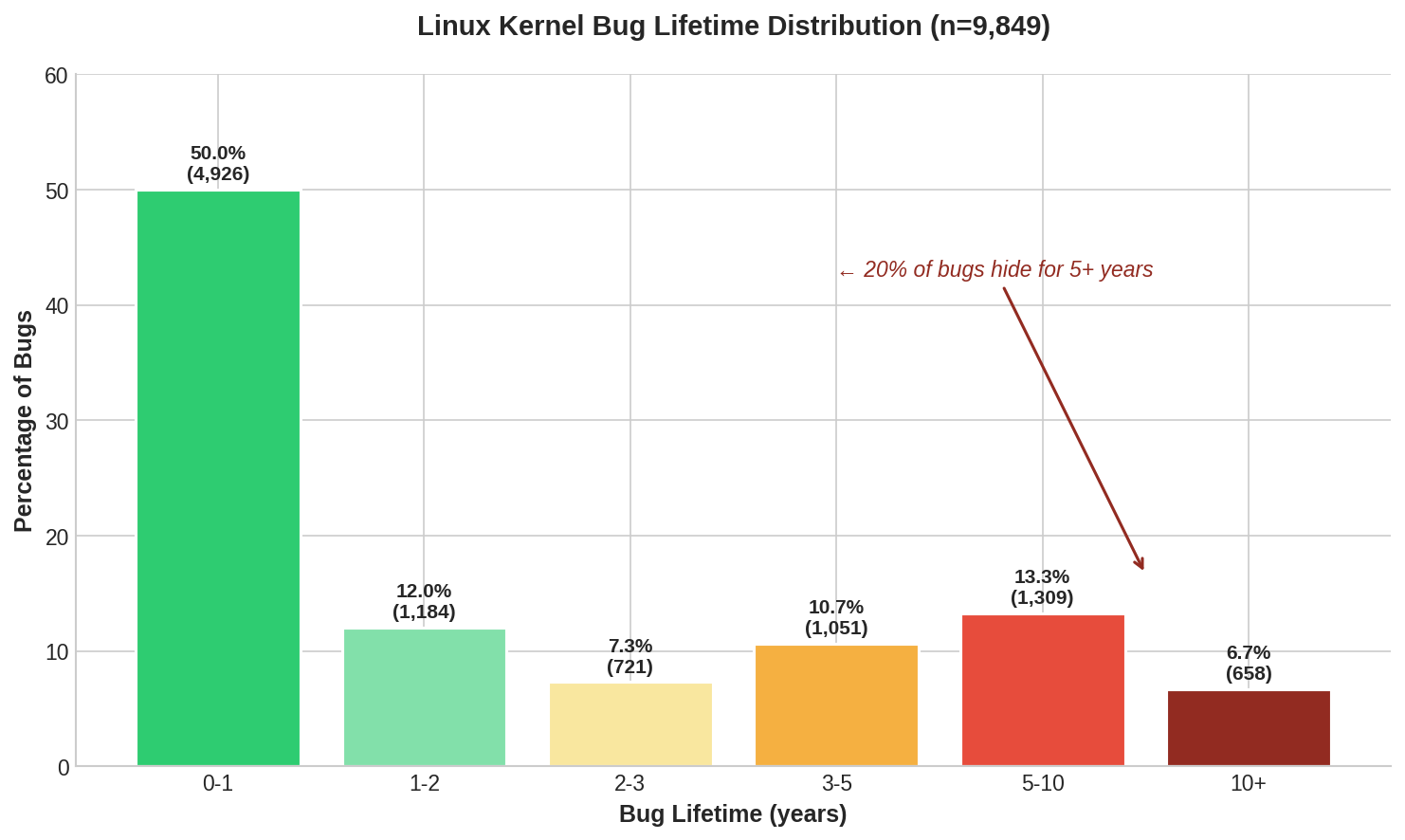
Jenny Guanni Qu, a researcher at Pebblebed, analyzed 125,183 bugs from 20 years of Linux kernel development history (on Git). The findings show that the average bug takes 2.1 years to find. The longest-lived bug, a buffer overflow in networking code, went unnoticed for 20.7 years!
The research was carried out by relying on the Fixes: tag that is used in kernel development. Basically, when a commit fixes a bug, it includes a tag pointing to the commit that introduced the bug.
Jenny wrote a tool that extracted these tags from the kernel's git history going back to 2005. The tool finds all fixing commits, extracts the referenced commit hash, pulls dates from both commits, and calculates the time frame.
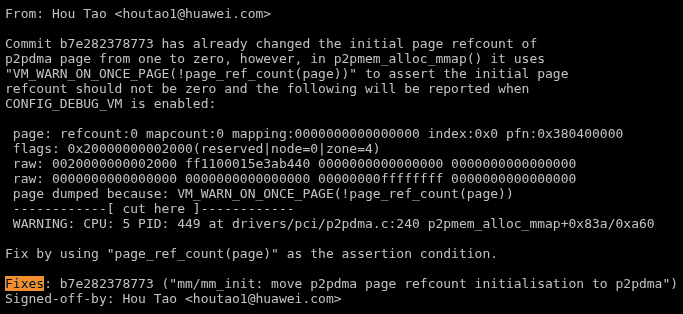
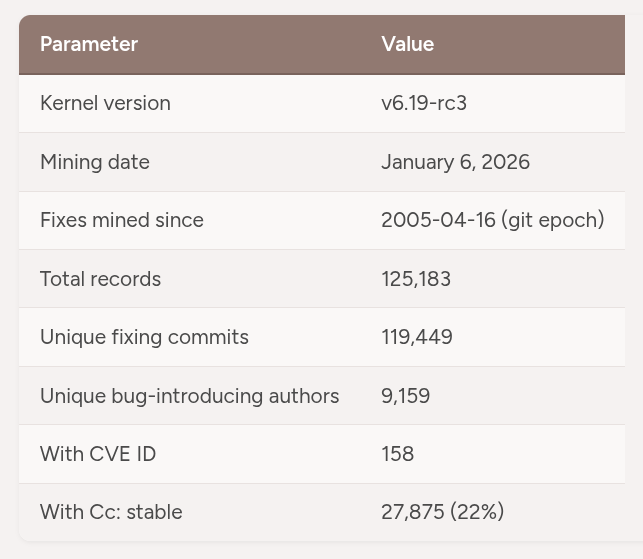
Example of how the Fixes: tag is used on the left, the dataset parameters used by Jenny on the right.
As for the dataset, it includes over 125k records from Linux 6.19-rc3, covering bugs from April 2005 to January 2026. Out of these, 119,449 were unique fixing commits from 9,159 different authors, and only 158 bugs had CVE IDs assigned.
Plus, she found out that different parts of the kernel show significant variation in how long bugs remain hidden. CAN bus drivers have the longest average at 4.2 years, followed by SCTP networking at 4.0 years. GPU bugs get caught fastest at 1.4 years, and BPF bugs are found within 1.1 years.
The research also found that incomplete fixes are common. Someone notices undefined behavior and ships a fix, but the fix does not fully address the problem. In one case, a 2024 fix for netfilter set field validation was incomplete, and a security researcher found a bypass a year later.
Jenny's research goes much deeper than what I covered here. She has also developed an AI model called VulnBERT that predicts whether a commit introduces a vulnerability. The detailed blog post linked above includes elaborate technical explanations on that; it is a must-read!
Suggested Read 📖: The First Rust CVE in Linux Kernel




