
What is a checksum?
A checksum is like the digital fingerprint of a file. In technical terms, a checksum is a small-sized datum from a block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage.
So a checksum is a long string of data containing various letters and numbers. As a Linux user, you’ll generally find them while downloading files from the web, e.g., Linux distribution images, software packages, etc.
For instance, the Ubuntu MATE download page includes an SHA-256 checksum for every available image.
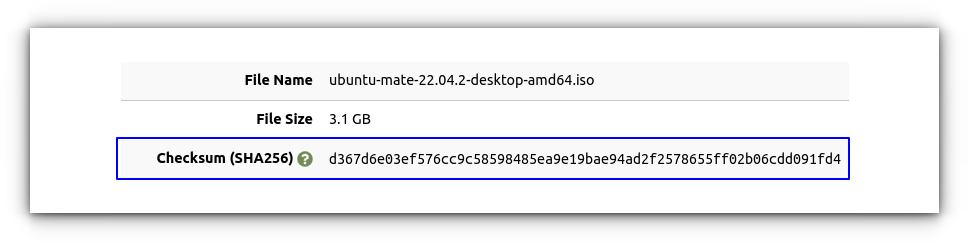
So after you’ve downloaded an image, you can generate an SHA-256 checksum for it and verify that the checksum value matches the one listed on the site.
If it doesn’t, your downloaded image’s integrity is compromised (maybe it was corrupted during the download process).
Each checksum is generated by a checksum algorithm. Without going into the technical details, let’s say it takes a file as input and outputs the checksum value of that file. There are various algorithms for generating checksums. The most popular checksum algorithms are:
Let’s see how to verify a checksum on Linux.
Method 1: Verify checksum in Linux using a GUI tool
If you’re looking for a graphical solution, you can use the GtkHash application. Your file manager can also verify checksum if you install the appropriate plugin.
The GtkHash app should work for all distros and desktop environments, so let's go with this method.
Installing GtkHash
To install GtkHash on your Ubuntu system, run the following command:
sudo apt install gtkhash
Now, you should select the checksum algorithms to use. Go to Edit > Preferences in the menu. Select the ones you’d like to use. Hit the Close button.
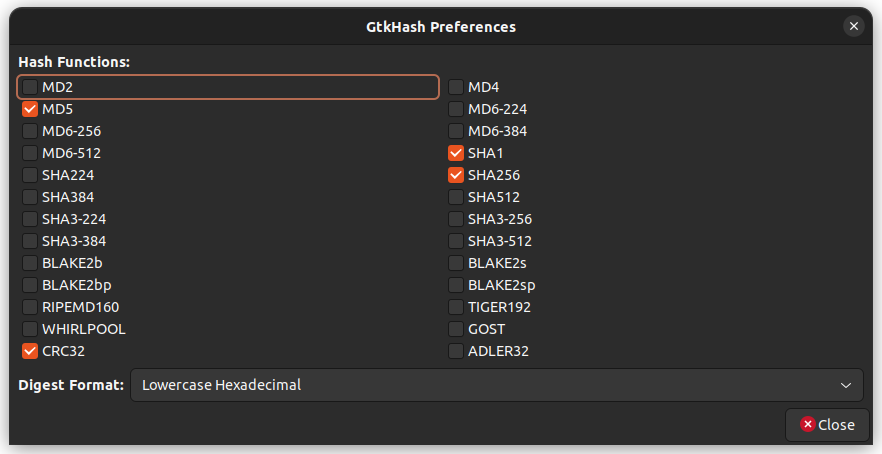
By default, MD5, SHA-1 and SHA256 are selected. You can see all the supported algorithms in the above screen.
Using GtkHash
Using GtkHash is quite straightforward.
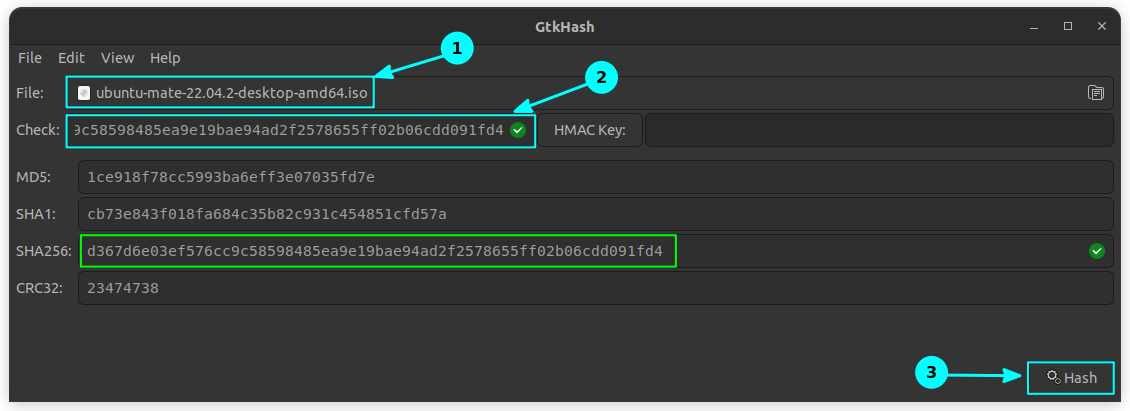
- Select the file you want to check.
- Get the Checksum value from the website and put it in the box, called “Check”.
- Click the Hash button.
- This will generate the checksum values with the algorithms you selected.
- If any one of them matches with that entered on the “Check” box, it will show a small tick sign beside it.
Here’s an example showing GtkHash generating a checksum for the Ubuntu MATE ISO image (Ubuntu Mate 22.04 ISO):
Method 2: Verify checksums via Linux command line
Every Linux distribution comes with tools for various checksum algorithms. You can generate and verify checksums with them.
The command-line checksum tools are the following:
- MD5 checksum tool is called md5sum
- SHA-1 checksum tool is called sha1sum
- SHA-256 checksum tool is called sha256sum
There are some more available, e.g., sha224sum, sha384sum, etc. All of them use similar command formats.
Let’s see an example using sha256sum. I’ll use the same “Ubuntu Mate 22.04” image file that I used before.
Generating and verifying SHA256 Checksum
First, go to the directory where the ISO image is stored:
cd ~/Downloads
Now, to generate the SHA-256 checksum, enter the following command:
sha256sum ubuntu-mate-22.04.2-desktop-amd64.iso
You’ll see the SHA-256 checksum in your terminal window! Easy, isn’t it?

If the generated checksum matches the one provided on the Ubuntu MATE download page, that will mean no data was changed while you downloaded the file – in other words, your downloaded file is not corrupted.
You don't have to match it character by character. Copy the value you got from the terminal. Now go to the webpage where the checksum is mentioned officially. Press CTRL+F on Firefox to open a search inside page. Now paste the checksum you have copied from the terminal to this find box.
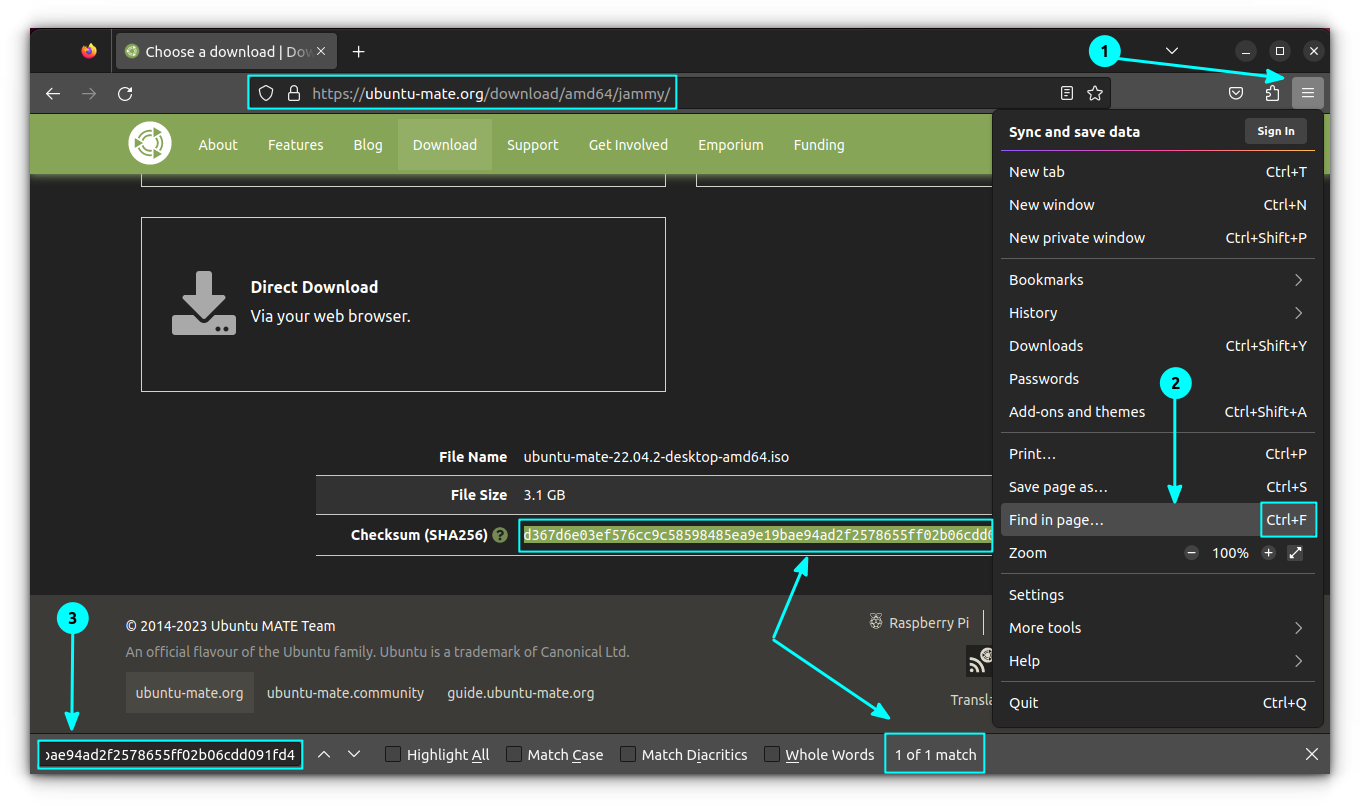
If the checksum you got is the right one, it will show a match on the website's find feature. That's it.
Generating and verifying checksum against a file
Some distributions, like Fedora, give you a checksum text file, which you can use to verify the integrity. You have to download the checksum file to the exact location where you have downloaded your ISO file.
Now, open a terminal there and enter:
sha256sum -c <name-of-text-file>
This will give you a message mentioning the ISO file is OK for use.

Bonus tip: Generate checksum file
If you have an ISO, which is verified, you can create a checksums text file, to check the integrity in the future, This will be handy if the ISO have been copied to multiple places. For this, create a checksums text file for your ISO.
sha256sum path-to-ISO-file > shasums.txt
Now, in later a time, you can verify this by pasting this file on the same location as the ISO and running:
sha256sum -c shasums.txt
It will print an ISO OK message.
Checksums of multiple ISO files
Hashes of multiple ISO files can be verified in one single command. For this, first go to the directory where you have saved all the ISO files. Now, open a terminal and run:
sha256sum *.isoThis will print the SHA value for the ISOs, which you can then verify.
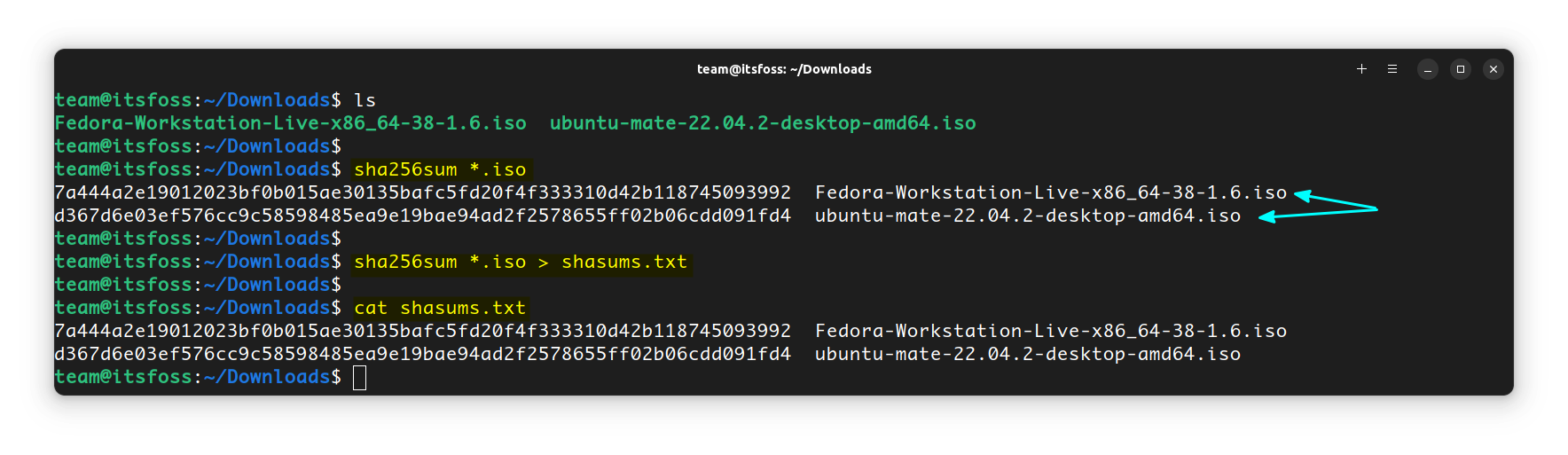
Also, you can save all the hashes into a file using:
sha256sum *.iso > shasums.txtCommands for other algorithms
The other tools mentioned work similarly.
| Command | Use |
|---|---|
| sha1sum filename.iso | Check and print the SHA-1 value |
| shasum -c checksums.txt | Read SHA-1 sums from the File and check them |
| md5sum filename.iso | Check and print the SHA-1 value |
| md5sum -c checksums.txt | Read MD5 sums from the File and check them |
Do you checksum?
One of the suggested steps while installing Linux is to verify the checksum of your Linux ISO. Do you always follow this step, or only do it when something goes wrong with the installation?


